SAP has just released the highest severity security notice of 2019. What can you do to protect your SAP landscape?
SAP has recently released a new set of security notes. What makes this round of notes unique is it includes the largest amount of notes to be released at once this year. Furthermore, it includes a note with a CVSS (SAP’s Product Security Response Team’s ‘Common Vulnerability Scoring System’) score of 9.9 – the highest rating of 2019. Let’s break these security notes down one by one to help you understand if your organization is affected and what you can do about it.
Highest Rated Vulnerability: Code Injected Into Working Memory
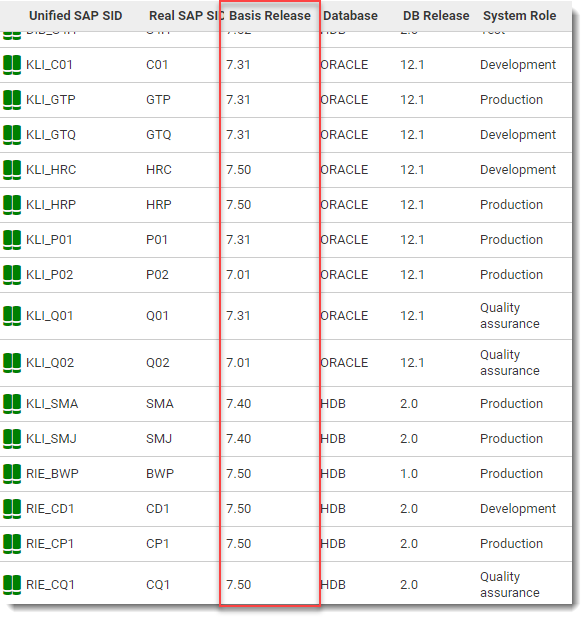
The first, and most critical note 2800779 – Remote Code Execution ‘RCE’ in SAP NetWeaver UDDI Server, scores a 9.9 on the CVSS scale – the highest to date this year. The vulnerability allows a hacker to inject code into the working memory of the system. This ranks extremely high as a threat because it’s ‘easy’ to inject and has a wide range of possible damages. The only way to secure your systems is to apply the patch within the note identified above. It is vital to note though that this vulnerability is only applicable to Netweaver systems at 7.1, 7.2, 7.3, 7.31, 7.4, and 7.5 release levels.
To quickly identify which systems in your landscape are vulnerable you can use Avantra, just head to your SAP systems list and review the ‘Basis Release’ column.
High Vulnerability: Server-side Request Forgery
The second vulnerability ranks as a 9.0 on SAP’s CVSS scale (Note #2813811 – Server-Side Request Forgery ‘SSRF’ in SAP NetWeaver Application Server for Java). Essentially, a potential hacker can access the Management Console of an SAP Java system. Once in, it allows the hacker to display log and trace files, profile parameters (including system settings and audit based settings), access to the Internet Communication Manager (ICM), display & control Java process and even more – it can completely start, stop, or restart the SAP system itself.
To mitigate the risk, the best option is to apply the patch SAP has provided. However, if immediate patching is not a viable option, it can still be alleviated by locking down your system through a specific profile parameter ‘jstartup/service_acl’ and making sure it does not contain ‘sap.com*’. Using Avantra this parameter can be continuously monitored to ensure it is properly configured and also send out a notification if is modified.
Furthermore, properly limiting system access using access control lists (ACL) will help control system connections. (See our recent blog about managing external connections.)
Denial of Service in SAP HANA Database
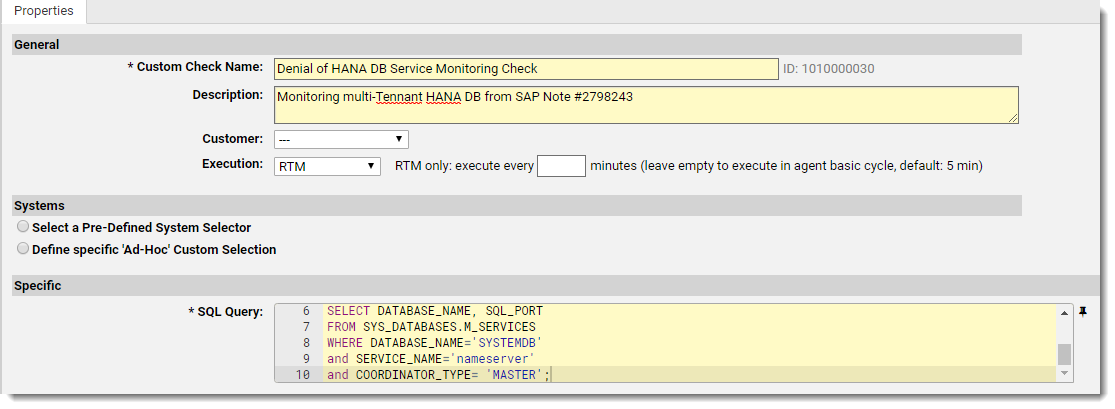
The third SAP security note #2798243 ‘Denial of Service in SAP HANA Database’ scores a 7.5 on SAP’s CVSS. This allows an attacker to send malformed connection requests to an SAP HANA system – similar to that of a DoS attack. This will lead to major interruptions of the HANA system and create availability issues within the system itself. SAP has provided patches to fix this issue, but patching is not always a viable, quick option for all organizations.
Limiting which connections can be accessed from outside systems will reduce the number of outside threats by restricting which SQL network ports can be accessed. These settings should then be continuously monitored to reduce the chance of a violation. Continuous monitoring of these settings can become a bit tricky especially with a multi-container SAP HANA database (as described here). This complex query can be easily implemented within minutes across all HANA environments in your SAP ecosystem by using Avantra’s SQL Query Custom Check to manage its deployment and continuous use.
Missing Authorization Vulnerability
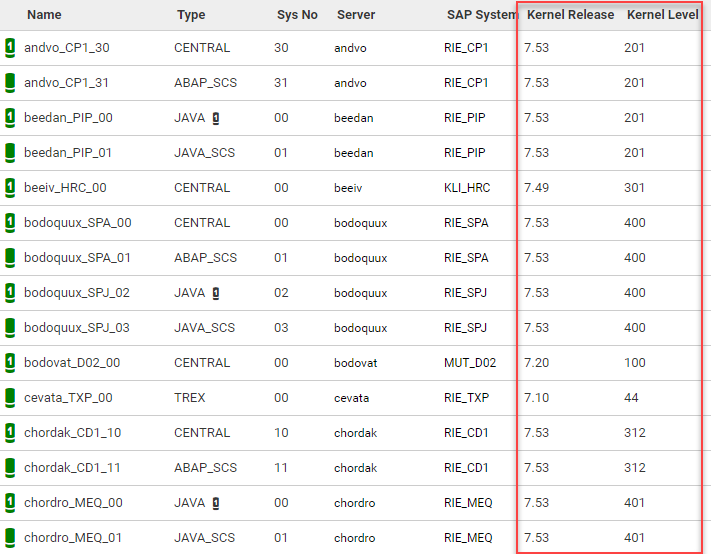
Lastly is SAP’s note #2798743 ‘Missing Authorization Check in SAP Kernel’. This issue affects ABAP based systems such as SAP NetWeaver, SAP ERP, and SAP S/4 HANA concerning a missing authorization vulnerability of the SAP kernel package. The solution has been provided in a patch for the disp+work package of the SAP kernel. For full resolution, please be sure to update the kernel patch as described in the note on both central and additional instances.
With Avantra, all vulnerable systems can easily be identified in the ‘System Instances’ list, including central instances and all related application servers – this is a vital step to complete vulnerability patching across your entire landscape. It is easy to miss an application server or complete system (even non-production), and leave a gap for hackers to enter.
If you have found this post interesting, you may want to check out our recent blog post, How to Mitigate 10K Blaze Threats.
If you are not using Avantra yet and would like to find out more, just fill out your details here and a member of our team will be in touch shortly