SAP has just announced a security vulnerability that gives an attacker a way to potentially compromise SAP Java systems, affecting confidentiality, integrity, and availability of the system
SAP recently pushed out the July patch day, with one patch ranking a CVSS (Common Vulnerability Scoring System) score of 10. A score of 10 is the top of the CVSS scale, indicating the importance of the vulnerability. The National Institute of Information Technology (NIST) is a US-based non-profit organization, whose mission is to help computer security incident response teams across the world. In their report, you can see the growth in the number of vulnerabilities since 2017. The amount of critical or high CVSS reported incidents have doubled, compared to the past levels and SAP systems are no exception.
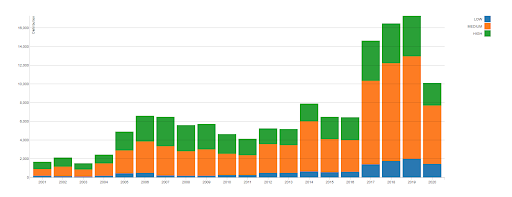
Source: NIST - CVSS Severity Distribution Over Time
You can read about how SAP uses the Common Vulnerability Scoring System in this post.
Why is this one so important?
The issue (fully documented by SAP in 2934135) basically gives an attacker access without an authentication check, creating a security hole and exposing the SAP system. It allows them to execute configuration tasks to perform critical actions, including highly privileged user creation, resulting in compromised security, confidentiality and potential availability of the system.
It is important to note that this is only valid on Java systems v. 7.3-7.5 that are exposed to the public (internet). The unfortunate news is Java systems are typically used in external facing portals for company employees, distributors, and customers that may not be on the secure internal network.
Even for those organizations that do not have any external facing systems, be sure to keep an eye on your Solution Manager. Depending on how the network is architected around SolMan, there is a chance it is configured with an outbound opening for SAP support to access the systems. Being that Sol Man is a dual-stack, there is a Java instance that might be susceptible to this vulnerability.
What should you do?
First off, be sure to read the SAP note and be prepared to implement the patch, if required following your organization’s change control policies. Then it’s off to find which systems fall within the range of versions that need to be patched. For very large enterprises and SAP Managed Service Providers, responsible for managing hundreds or thousands of systems, logging into each Java instance individually to identify which systems are vulnerable could take a lifetime.
What should Avantra Customers do?
With Avantra, finding the vulnerable systems is just a click away within the list of SAP systems or instances, either sorting by the version or searching via the search box.
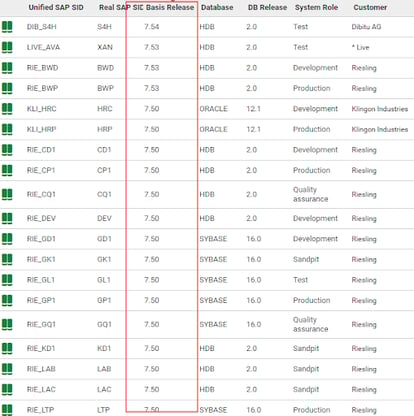
Also, if you are utilizing Avantra’s integration to a ServiceNow CMDB, the version can easily be retrieved within ServiceNow.
Please let us know if you would like to see how Avantra can help in making your SAP management easier.
PS.
If you missed these couple of past notifications, you may want to make sure your systems are protected:
Photo by Mika Baumeister on Unsplash







