New ICMAD bugs require immediate attention and patching for SAP systems. The dust has not yet settled on the CVSSv3 10.0 score Log4j security vulnerability, which has been keeping IT employees across all businesses very busy since December 2021.
Read this article to learn more about the CVSSv3 10.0 score Log4j security vulnerability.
Three SAP security vulnerabilities
Last week, a new group of three security vulnerabilities were published by SAP, which all relate to SAP’s Internet Communication Manager (ICM). Once again, one of these vulnerabilities has a CVSS v3.0 base score of 10/10. In contrast to Log4j, the latest threats only impact SAP customers, but they need immediate attention.
How to protect your SAP systems
Why are the new SAP vulnerabilities so critical?
SAP ICM is one of the most important components of SAP’s NetWeaver application server because it connects to the internet. The ICM’s main purpose is to handle HTTP(S) requests server side. In the SAP NetWeaver application server, ICM is active by default Therefore, it’s typically used in network security zones (as part of SAP Web Dispatcher) to separate the internet from the application server.
The so called ICMAD (Internet Communication Manager Advanced Desync) vulnerabilities were discovered and reported to SAP by Onapsis Research Labs:
- CVE-2022-22536 (CVSSv3 10.0)
- CVE-2022-22532 (CVSSv3 8.1)
- CVE-2022-22533 (CVSSv3 7.5)
SAP Note 3123396 describes the threat as “the worst vulnerability.” When you look at the CVSS v3.0 base vector, it’s clear why it’s scored as high as 10.0. Let’s break it down quickly…
The vulnerability:
- is exploitable over the network.
- has a low attack complexity.
- can be exploited with a simple and single HTTP request.
- requires no privileges or user interactions.
The impact is rated as high on all three impact classes: confidentiality, integrity, and availability. That is truly a worst case scenario - one attack can lead to a fully compromised system.
Onapsis puts it this way in the executive summary of their white paper:
Therefore, with this most critical issue, unpatched SAP NetWeaver applications (JAVA/ABAP) reachable through HTTP(S) are vulnerable to it, as well as any application sitting behind SAP Web Dispatcher, such as S/4HANA.
What is the solution to these SAP security vulnerabilities?
All three CVEs are resolved by patching the SAP Kernel and the SAP Web Dispatcher. Note: 3123396 links to a workaround as well, but this can only be considered as a temporary solution. Customers need to patch as soon as possible.
How does Avantra help improve SAP security?
With its automatic download of SAP HotNews and evaluation, Avantra shows all vulnerable systems in one list.
.png?width=567&name=Untitled%20design%20(13).png)
Users can simply use the SAP automatic kernel upgrade tool within Avantra. Download the updated kernel packages from SAP, upload to Avantra, and the kernel patch automation tells you which system it can be applied to.

You then have the option to apply the kernel upgrade immediately or schedule it for later. If your SAP system is configured to support the rolling kernel upgrade, Avantra does this as well.
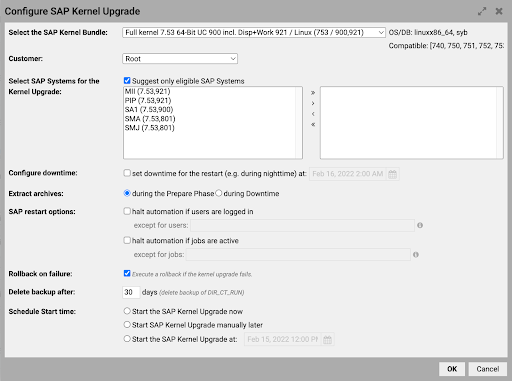
Respond quickly to SAP security threats
In a world of digital transformation, it is increasingly important to respond quickly to security threats. At Avantra, we believe that intelligent automation is the key to running secure SAP landscapes.
Learn more about how to prevent SAP security vulnerabilities in our ebook.







.png?width=567&name=Untitled%20design%20(13).png)


